Are you worried about the security of your crypto wallets? In today’s digital landscape, protecting your digital assets from cyber threats is crucial. This comprehensive guide, “How to Secure Your Crypto Wallets Against Cyber Threats,” will equip you with the knowledge and strategies to safeguard your cryptocurrency investments from hackers, phishing scams, and other online threats. Learn about best practices for wallet security, including choosing the right wallet type, implementing strong passwords and two-factor authentication (2FA), and recognizing and avoiding common security risks. Don’t let your hard-earned crypto become a victim – let’s dive in and learn how to keep it safe!
Why Cybersecurity is Crucial for Crypto
The cryptocurrency world, while offering exciting opportunities, is unfortunately also a prime target for cybercriminals. Security is paramount because cryptocurrencies, unlike traditional banking systems, are largely decentralized and irreversible. Once your funds are gone, recovering them is exceptionally difficult, if not impossible.
Cybersecurity threats in the crypto space range from phishing scams and malware to sophisticated hacking attacks targeting exchanges and wallets. These attacks can result in the complete loss of your digital assets, impacting your financial well-being significantly.
Robust cybersecurity practices are not just advisable; they’re essential. They protect your private keys, which are the passwords to your cryptocurrency holdings. Without strong security measures, your private keys can be compromised, leading to theft. This is why employing strong passwords, using reputable wallets, and staying vigilant against phishing attempts are all crucial aspects of protecting your investments.
Ultimately, the decentralized nature of cryptocurrencies means that you are solely responsible for the security of your assets. Prioritizing cybersecurity isn’t just about protecting your money; it’s about protecting your financial future.
Tips for Choosing Secure Wallets

Choosing the right crypto wallet is crucial for safeguarding your digital assets. Consider these factors to ensure strong security:
Wallet Type: Hardware wallets offer the highest level of security due to their offline nature. Software wallets (desktop or mobile) provide convenience but require extra caution. Consider your comfort level with technology and the value of your crypto holdings when making this decision.
Reputation and Security Features: Research the wallet’s reputation thoroughly. Look for wallets with a strong track record, open-source code (allowing for community scrutiny), and robust security features like multi-factor authentication (MFA), biometric logins, and regular security updates.
Backup and Recovery: Understand the wallet’s backup and recovery process. Ensure you have a secure method of storing your seed phrase (never store it digitally) and understand how to recover your funds in case of device loss or damage.
Privacy Features: If privacy is a concern, explore wallets that prioritize anonymity and offer features like privacy-enhancing technologies.
Customer Support: Choose a wallet provider with responsive and helpful customer support in case you encounter any issues.
By carefully considering these factors, you can significantly reduce your risk of cyber threats and protect your cryptocurrency investments.
How to Detect Malware in Wallet Software

Protecting your cryptocurrency requires vigilance. Malware in wallet software can silently drain your funds, so learning to detect it is crucial. Unusual behavior is a key indicator. Does your wallet software suddenly run slower than usual, consume excessive resources, or display unexpected pop-ups or prompts?
Security software is your first line of defense. Ensure your antivirus and anti-malware programs are up-to-date and regularly scan your system, including your wallet software files and associated directories. Look for unusual processes running in your task manager that you don’t recognize, especially those consuming a high percentage of CPU or memory.
Verification is paramount. Always download wallet software from the official website or trusted app stores. Be wary of links from emails or suspicious websites. Verify the software’s digital signature to ensure its authenticity. Check online forums and communities for reports of malware affecting your specific wallet software.
Regular backups and offline storage of your seed phrases are essential. If your wallet software is compromised, having backups minimizes the damage. Never store your seed phrases on your computer or devices connected to the internet. Employ a robust password manager and use strong, unique passwords for all your accounts.
Finally, stay informed. Regularly check for security updates for your wallet software and operating system. Be aware of emerging malware threats targeting cryptocurrency wallets and stay updated on best practices for online security.
Avoiding Phishing Scams in Crypto
Phishing is a major threat in the crypto world. Scammers often impersonate legitimate exchanges or projects to steal your private keys, seed phrases, or other sensitive information. They may send emails, text messages, or even create fake websites that look incredibly similar to the real thing.
To avoid falling victim, be incredibly cautious. Never click on links in unsolicited emails or texts claiming to be from a crypto exchange or project. Always independently verify the legitimacy of any website by manually typing the URL into your browser, checking for a secure connection (HTTPS), and looking for security indicators like SSL certificates.
Before entering any sensitive information, carefully examine the website for any irregularities. Look for misspellings, grammatical errors, or unusual design elements that might indicate a fake website. Also, be wary of unexpected requests for your private keys or seed phrases. Legitimate organizations will never ask for this information directly.
Enable two-factor authentication (2FA) on all your crypto accounts. This adds an extra layer of security, making it much harder for scammers to access your accounts even if they obtain your password.
Finally, stay informed about the latest phishing techniques. Follow reputable crypto news sources and community forums to learn about emerging threats and best practices for protecting yourself.
The Role of Multi-Signature Wallets
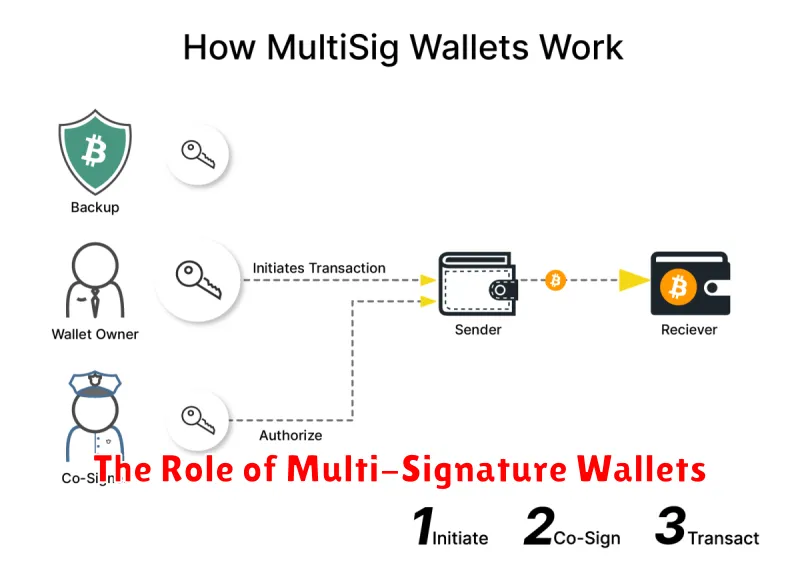
Multi-signature wallets significantly enhance cryptocurrency security by requiring multiple approvals for transactions. Instead of a single private key controlling access, multiple keys are needed, each held by a different individual or device.
This setup dramatically reduces the risk of unauthorized access. Even if one key is compromised, the transaction won’t be approved without the others. This is particularly crucial for managing large sums of crypto or shared organizational funds.
There are various types of multi-signature setups, allowing for flexibility in managing access. You can configure it to require 2 out of 3 signatures, 3 out of 5, or any other combination that suits your risk tolerance and security needs. The more signatures required, the higher the level of security, but also the more complex the transaction process becomes.
Implementing a multi-signature wallet adds an extra layer of protection against phishing scams, malware attacks, and even internal theft. It forces a collaborative approach to fund management, thereby making it far more resilient against cyber threats.
Backing Up Wallets for Recovery
Losing access to your cryptocurrency wallet can be devastating. Regular backups are crucial for recovery. This involves creating copies of your wallet’s seed phrase, private keys, or recovery data, depending on the type of wallet you use.
Never store your backup digitally on your computer or phone. These devices are vulnerable to malware and theft. Instead, opt for offline, physical storage. This could include writing the information on multiple pieces of paper and storing them in separate, secure locations, using a hardware security device (like a metal plate) to etch the information, or employing a password manager with strong encryption and offline access.
Consider using a multi-signature wallet for enhanced security. This requires multiple signatures to authorize transactions, reducing the risk of unauthorized access even if one backup is compromised. Remember to keep your backup copies safe from fire, water, and theft. Regularly verify your backups are intact and easily accessible – you don’t want to discover a corrupted file during a crisis.
The method you choose depends on your comfort level and risk tolerance. Prioritize security and redundancy. A well-executed backup strategy is your best defense against the loss of your cryptocurrency holdings.
Best Practices for Keeping Your Private Keys Safe
Your private keys are the foundation of your cryptocurrency security. Losing them means losing access to your funds—permanently. Therefore, safeguarding them is paramount.
Never share your private keys with anyone. Legitimate services will never ask for them. Treat them like your banking password—the utmost secrecy is essential.
Use a hardware wallet. These physical devices store your private keys offline, offering significantly enhanced security compared to software wallets. They are the gold standard for protecting large amounts of crypto.
If using a software wallet, choose reputable providers with strong security reputations and robust features like two-factor authentication (2FA). Regularly update the software to benefit from the latest security patches.
Employ strong, unique passwords for all your wallets and related accounts. Avoid using the same password across multiple platforms. Consider using a password manager to help you create and manage complex passwords safely.
Regularly back up your private keys, but store these backups securely and offline. Consider using multiple methods of backup, like physical copies in secure locations, and encrypted digital backups. Never store your backups on your computer or easily accessible online storage.
Be wary of phishing scams. Cybercriminals often try to trick users into revealing their private keys. Never click on suspicious links or download attachments from unknown sources. Verify the legitimacy of any communication before taking action.
Stay informed about the latest security threats and best practices. The cryptocurrency landscape is constantly evolving, so continuous learning is crucial for protecting your assets.

